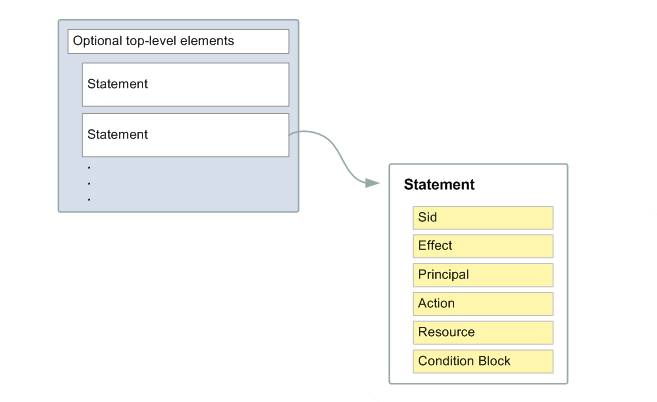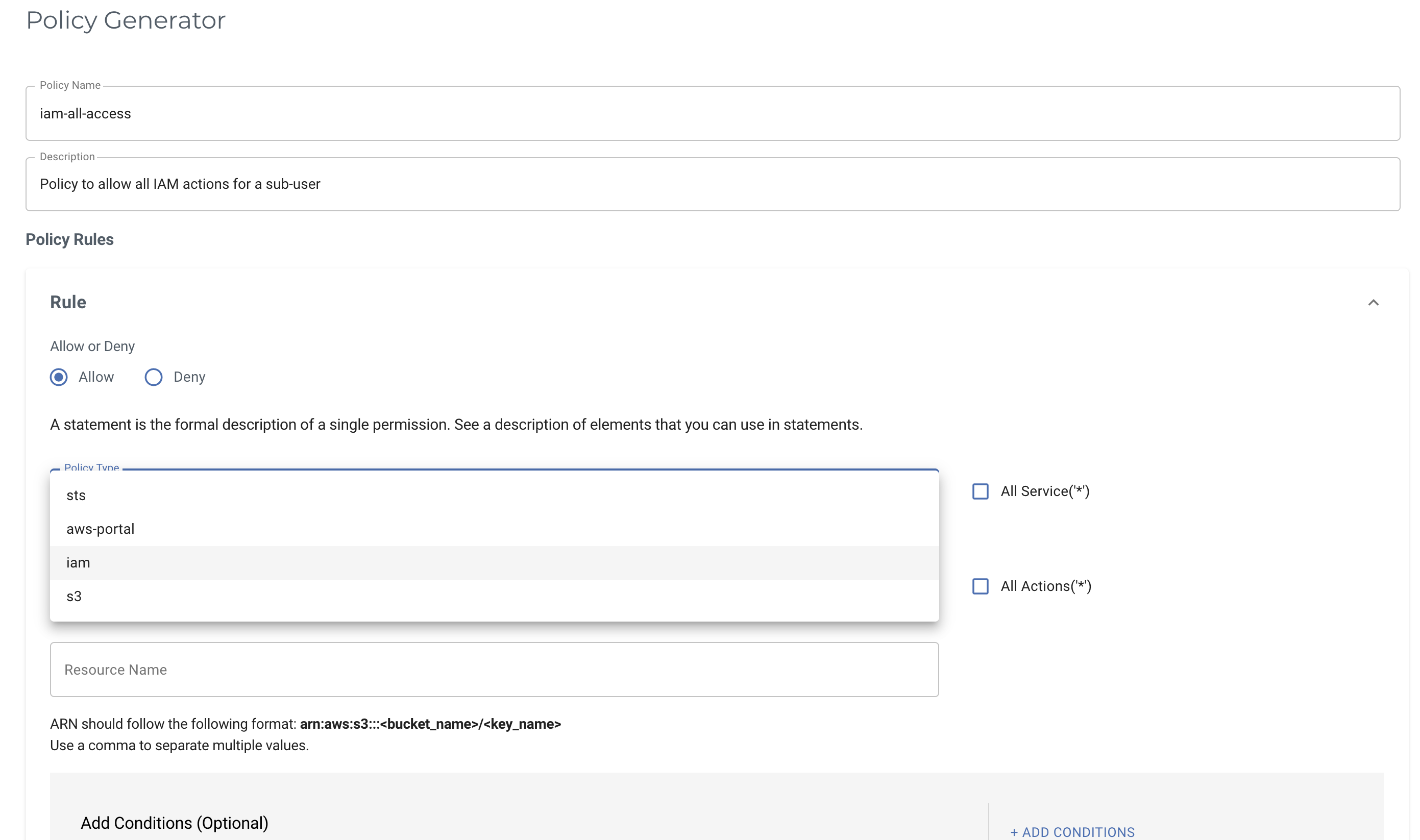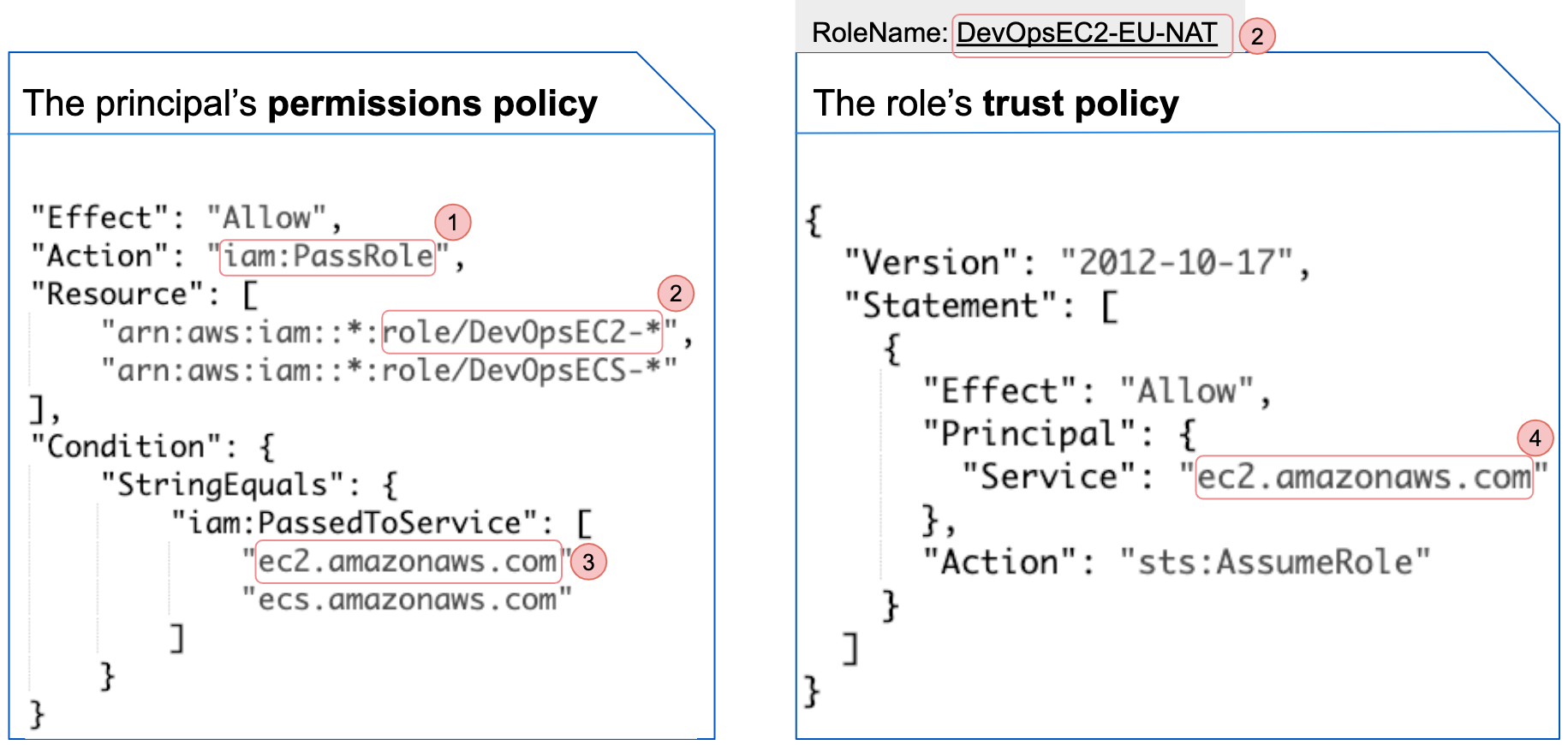
Unit 42 Cloud Threat Report: Misconfigured IAM Roles Lead to Thousands of Compromised Cloud Workloads
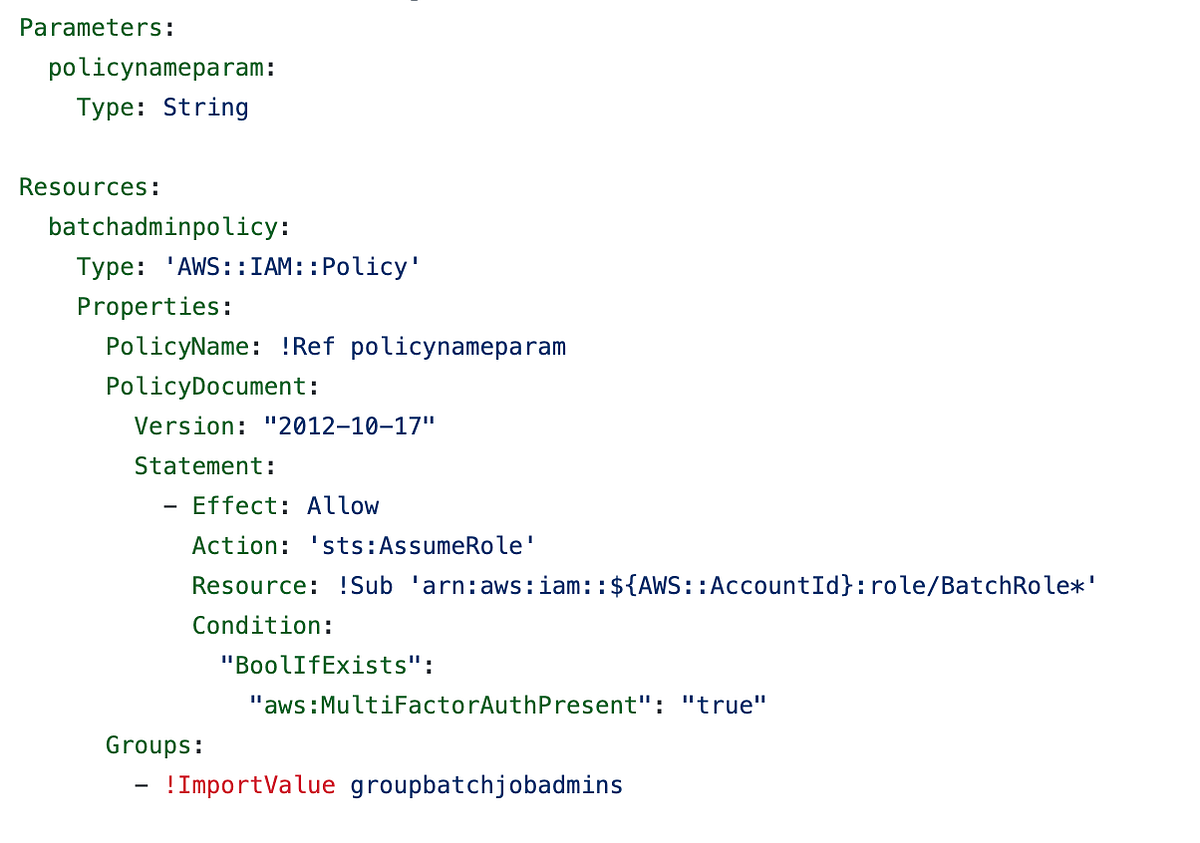
Adding Conditions to AWS IAM, Resource, and Trust Policies | by Teri Radichel | Cloud Security | Medium
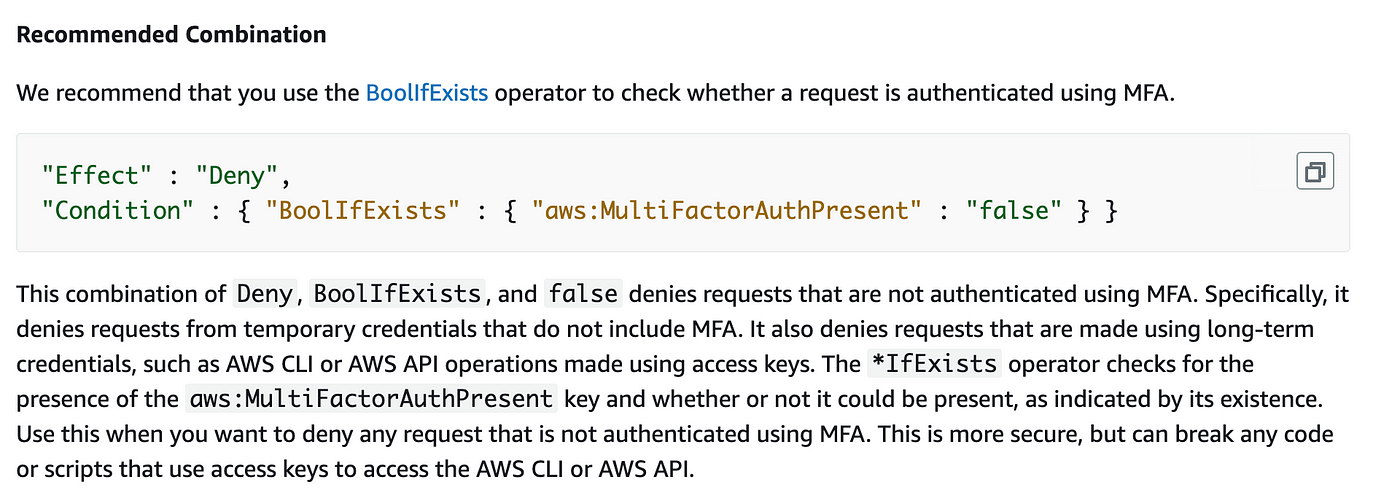
Adding Conditions to AWS IAM, Resource, and Trust Policies | by Teri Radichel | Cloud Security | Medium